OverView
Le médecin généraliste de votre cybersécurité.
« OverView analyse les résultats de vos outils, pose le diagnostic et vous oriente vers le bon spécialiste.»
Alimentez GLPI, EasyVista, iTop...
« OverView a permis aux équipes de gagner du temps dans leurs tâches quotidiennes. Notre CMDB se met à jour automatiquement grâce à l’information consolidée remontée dans l’outil. C’est un avantage précieux dans le dialogue des équipes Cyber et IT entre elles. »
Karim Bensaada, Directeur du numérique - Métropole Européenne de Lille
Reporting DSI/RSSI prêt à l'emploi
« Avant, nous avions l’information, mais pas la vision globale. Nous disposons désormais d’une vision unifiée et d’indicateurs pertinents, ce qui nous fait gagner un temps précieux. Je recommande OverView pour reprendre le contrôle sur ses actifs et simplifier le pilotage de la sécurité. »
Thibault Decroix, Responsable IT - DV Group
Avec OverView,
exploitez votre inventaire
Collectez sans agent toutes vos données IT et Cyber (structurées ou non) depuis vos outils existants, on-premise comme SaaS. OverView centralise automatiquement les données d'inventaire, de vulnérabilités, de configurations et de contexte métier dans une base unique via nos connecteurs dédiés.
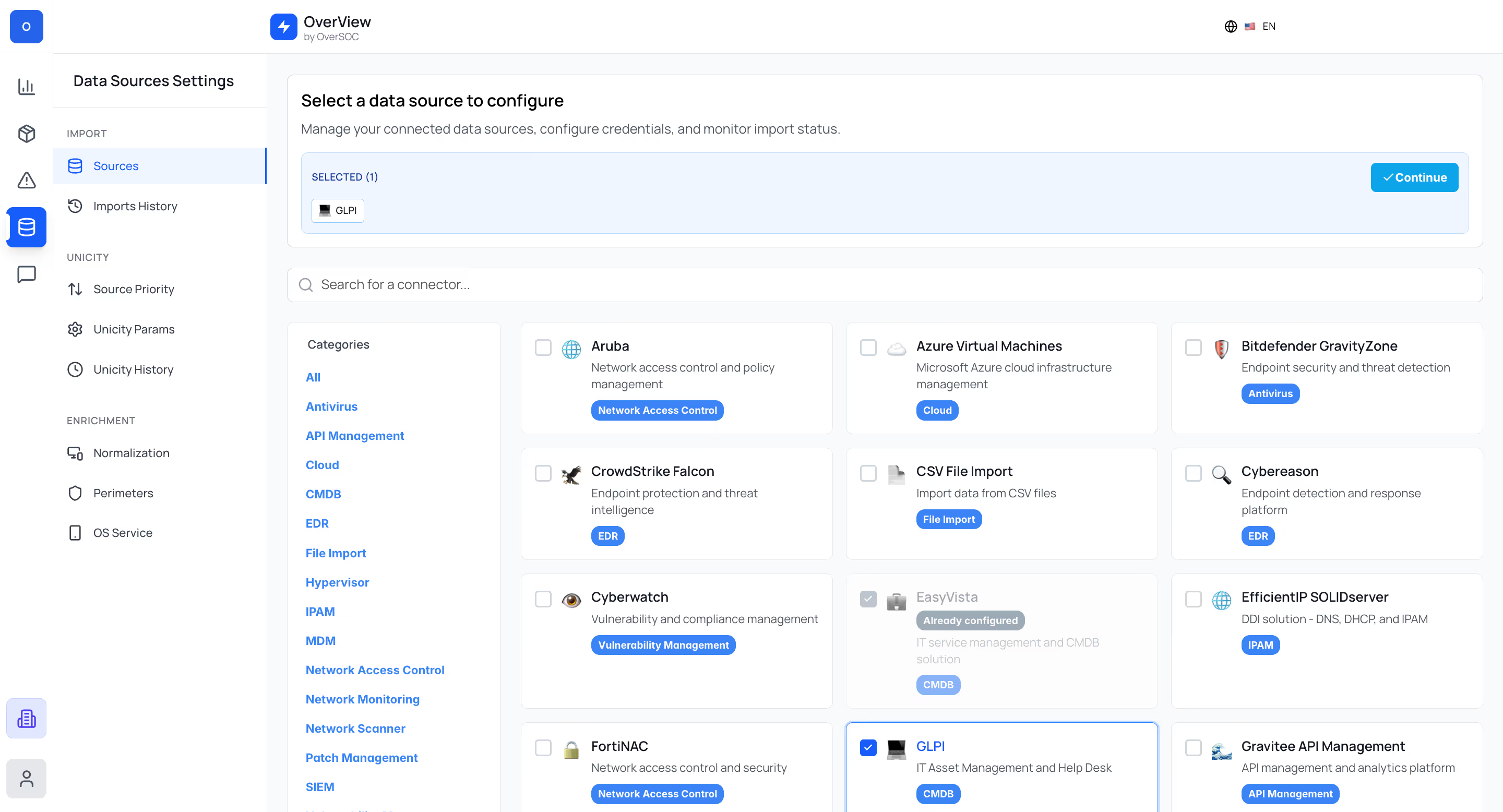
Finis les allers-retours entre outils ! OverView agrège et normalise automatiquement toutes vos données dans un référentiel unique, couvrant l'intégralité de votre parc IT, y compris le shadow IT.
Accédez instantanément à la vue 360° de chaque asset : configuration, vulnérabilités, criticité, contexte... En exploitant toutes les données de votre SI, détectez les assets non référencés et obtenez une vision exhaustive.
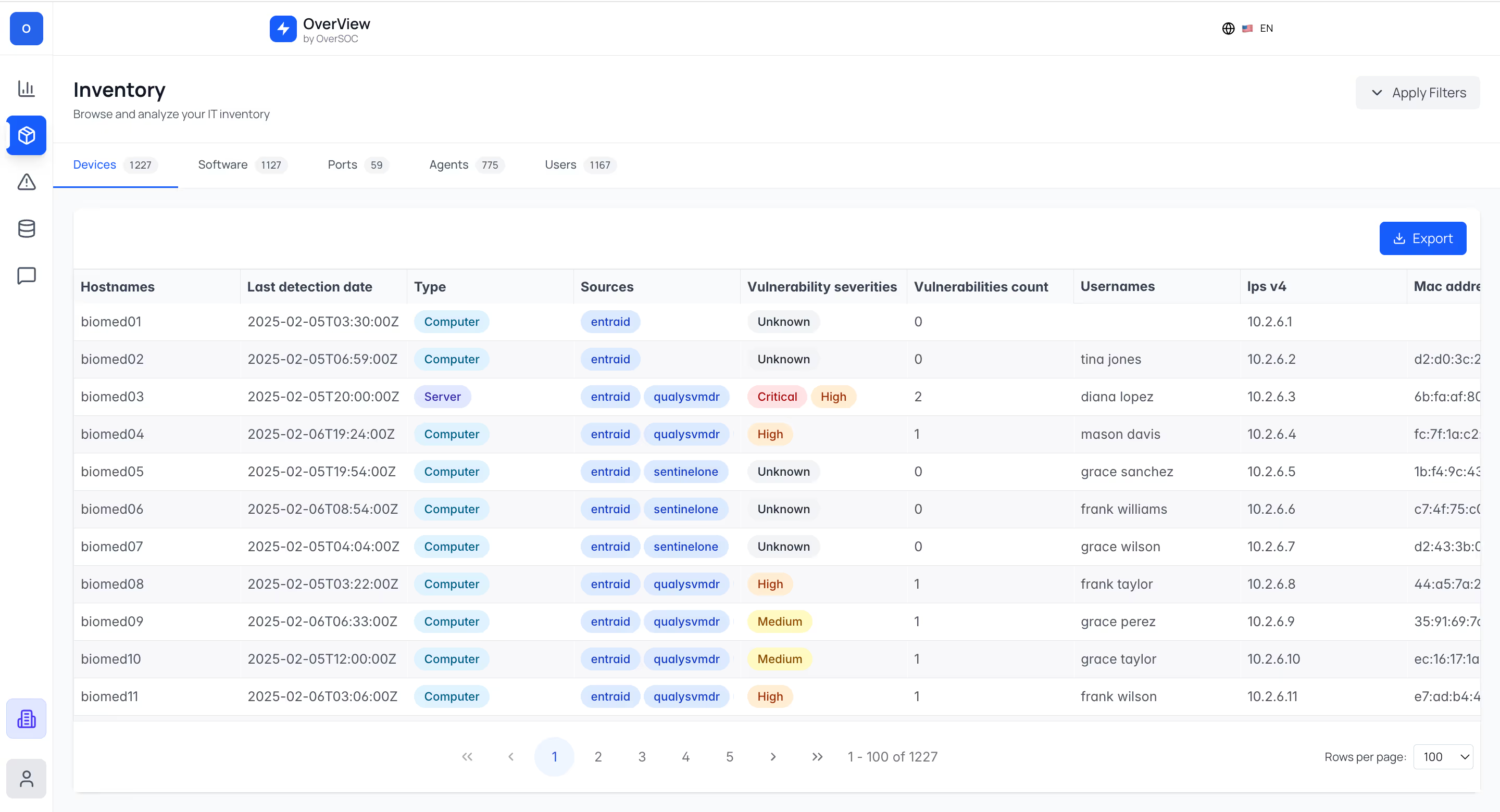
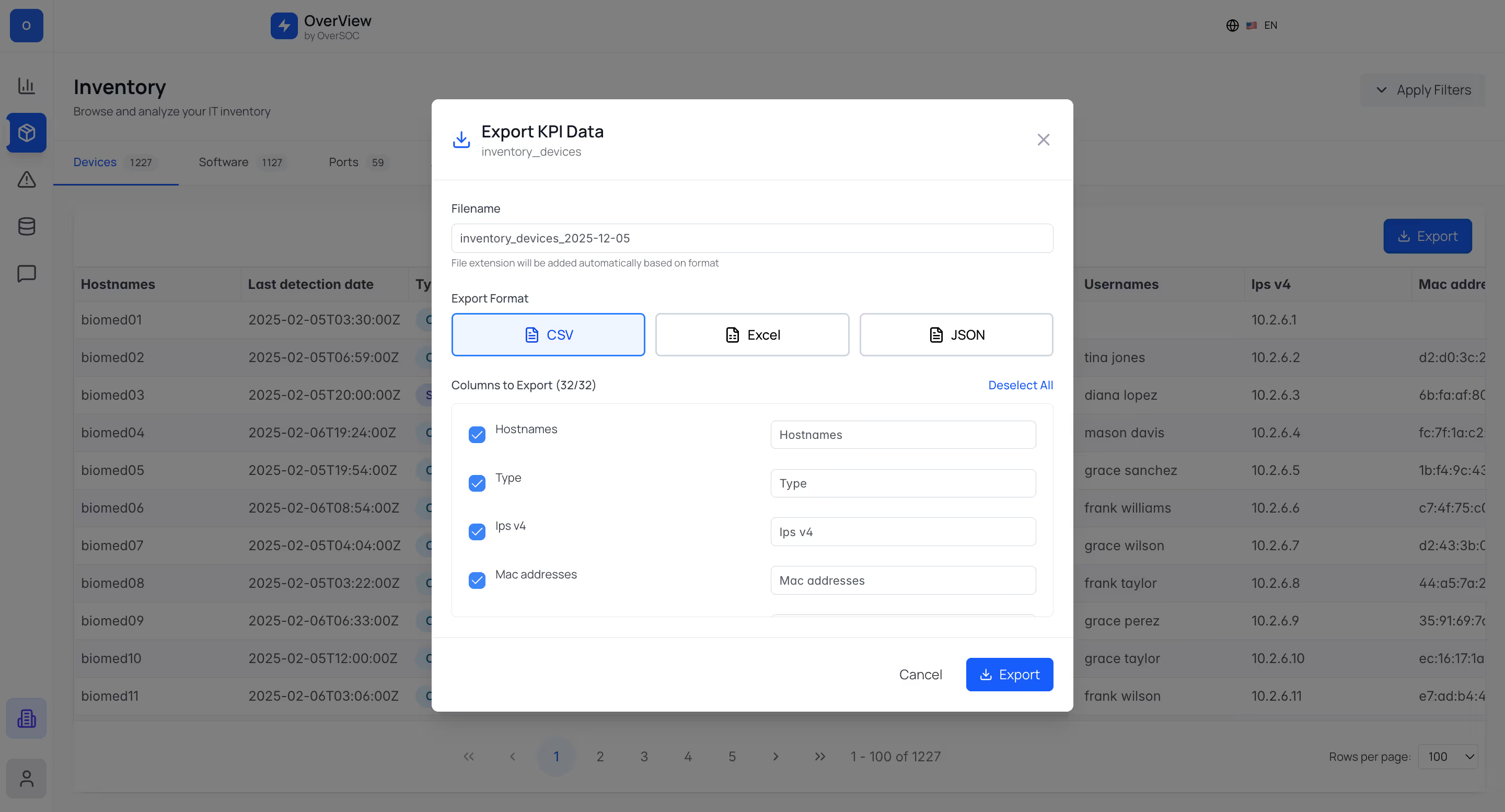
Exportez vos données unifiées vers n'importe quel outil, dans le format de votre choix (CSV, JSON, API...).
Alimentez automatiquement votre CMDB ou ITSM (ServiceNow, GLPI, EasyVista, Jira...) avec des données exhaustives et contextualisées, mises à jour quotidiennement. Finis les inventaires obsolètes : votre référentiel reste fiable en permanence.
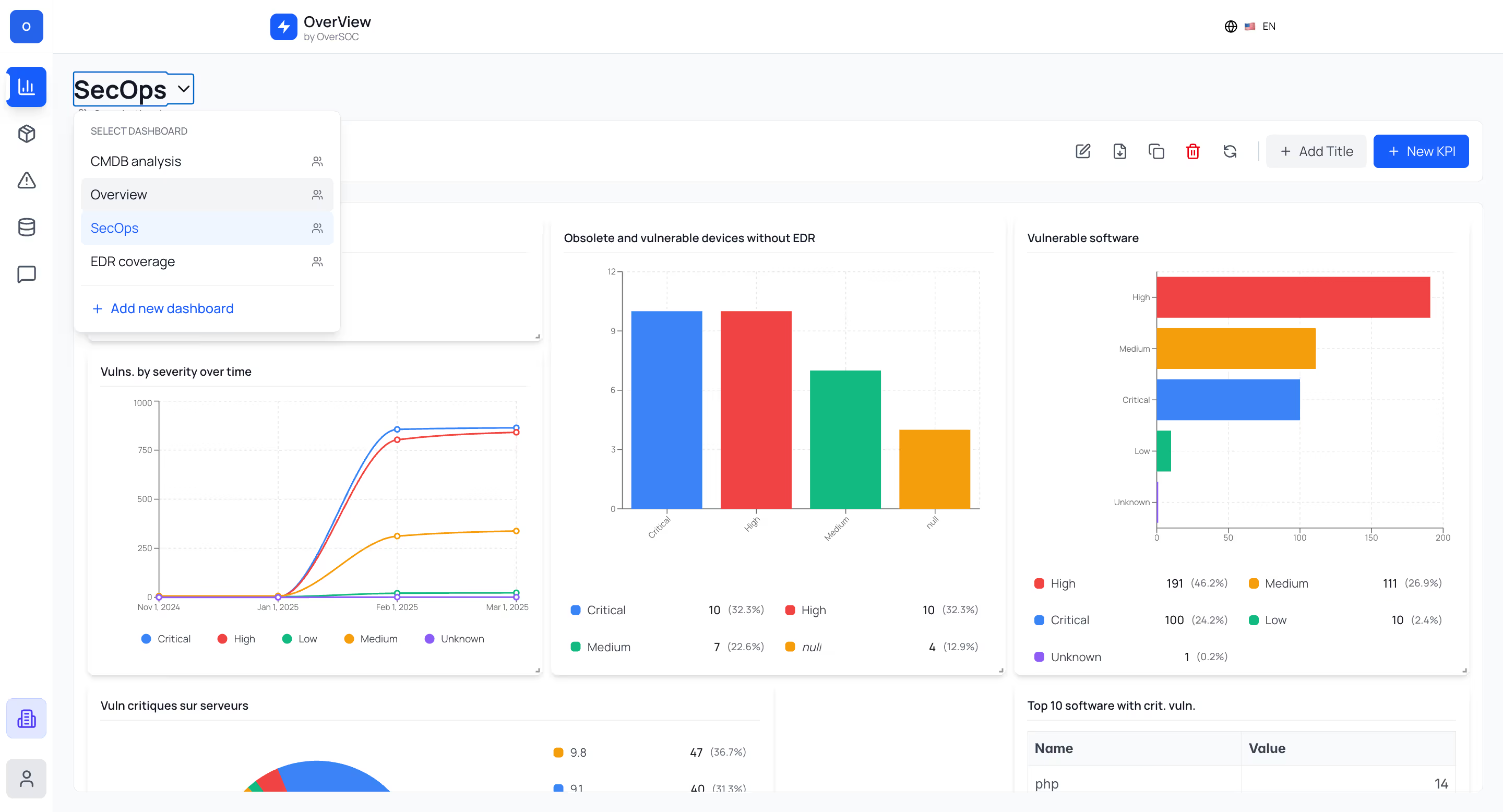
Bénéficiez de l'expertise de vos pairs : exploitez des tableaux de bord prêts à l'emploi et éprouvés par nos clients.
Créez n'importe quel KPI en croisant vos données multi-sources de façon simple et intuitive. Vérifiez instantanément votre conformité (NIS 2, ISO 27001, Guide d'hygiène de l'ANSSI...) grâce à notre bibliothèque de tableaux de bord métiers.
.png)


Attack Surface Management : livre blanc OverSOC, en collaboration avec le CESIN
Télécharger le livre blancUne équipe située sur le Campus Cyber Hauts-De-France

En tant qu'acteur local ancré dans l'écosystème cyber de la région Hauts-de-France, OverSOC bénéficie d'une position privilégiée pour comprendre les enjeux spécifiques auxquels les entreprises de la région sont confrontées, en les aidant à mettre en place des mesures de prévention efficaces pour protéger leurs actifs et renforcer leur posture de sécurité, leur agilité et leur résilience.
.webp)
























.png)
.png)
.png)






















